Become a Vendor Assessment Jedi Using the NIST Cybersecurity Framework
Written by Randy Lindberg, Founder and Managing Partner with Rivial Security (A Quantivate Partner)
 There are some ordinary steps that you can take to assess vendor due diligence. But, you donât want to be ordinary...
There are some ordinary steps that you can take to assess vendor due diligence. But, you donât want to be ordinary...
To be a Vendor Assessment Jedi, use the NIST Cybersecurity Framework, you must!
Vendor due diligence is the process of ensuring that the use of external IT service providers and other vendors does not create unacceptable potential for business disruption or negative impact on business performance.
To accomplish the objective of vendor due diligence, your credit union needs to:
- Gather company details such as ownership specifics, company size, products offered, and location
- Understand the companyâs financial position, or rather, is this vendor financially stable enough to service your needs for at least 1 to 2 years
- Know if the vendor will live up to their promises in terms of reputation via BBB ratings, CFPB complaints, and reference checks
- Know how well the vendor is going to protect your data
Vendors that provide IT Services have additional due diligence requirements, your credit union needs to:
- Make sure that contract language includes information on the right to audit, data security measures, and data ownership
- Define specific security considerations and incident response procedures. Additionally, for cloud-based IT service there are additional data security questions that need answers (cloud-based IT service that the NIST 800-145 definition is referred to in FFIEC guidance1)
Ultimately, your credit union, as the entity responsible for assessing vendor due diligence, must understand the vendorâs cybersecurity stance. How do you determine a vendorâs cybersecurity position? You can request an audit of their security controls, which typically comes back in the form of an SSAE 16 report.
SSAE Â stands for âStatement on Standards for Attestation Engagements.â The SSAE 16 is delivered in the form of Service Organization Controls (SOC) reports. There are several report types, but the two most common and important are:
- SOC 1 Type 2, which reports on the design and effectiveness of internal controls over financial reporting; and
- SOC 2 Type 2, which reports on the design and effectiveness of âtrust service principlesâ such as security, confidentiality, and availability.
In most cases, the SOC 2 Type 2 is the best report for assessing cybersecurity. The SOC 1 report, however, is the most commonly used report. Not all SSAE 16 reports are the same because there is discretion as to which and how many of the five (5) trust services principles are actually examined and reported on during a SOC 2 engagement. You have to dig into some details to understand what is being reported.
For example, if an IT Service Provider has a SOC audit performed on their corporate network, but outsources application development and data center hosting, youâll essentially be left with a meaningless document.
The ordinary steps used to perform a SSAE 16 review are:
- Pinpoint findings without adequate management responses
- Provide complementary user entity controls to system owner and/or IT
But, you want to be extraordinary. By using the NIST Cybersecurity Framework in the following way, you can become a Vendor Assessment Jedi:
- Review the description of the vendorâs system addressed in the SSAE 16 report
- Search for âsubserviceâ to find the section where subservice organizations (i.e., any businesses that your vendor contracts with/outsources) are described
- Use function, category, or subcategory (depending on your technical expertise and comfort level) to ensure control objectives are covered
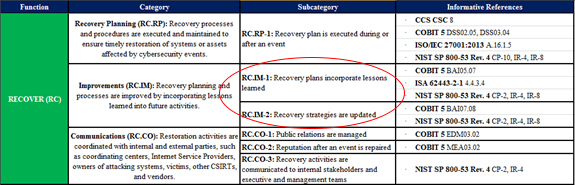
NIST Cybersecurity Framework Core Example
Using the partial image above, you could search through the SSAE 16 report in a structured manner using the Framework as a guide.
If you use the âsubcategoryâ component of the Framework, you would check the vendorâs report for a control objective that outlines âResponse plans incorporate lessons learnedâ (as highlighted in the example above) or something very similar. If there is sufficient content in the report, you can mark that subcategory is âin placeâ in your vendor cybersecurity assessment tracking documentation.
Using the NIST Cybersecurity Framework, in this way, to walk through vendor security audit reports provides a useful and efficient method to review vendor security controls.
To learn more about using the NIST Cybersecurity Framework to ensure proper vendor due diligence, register for the upcoming webinar, âAssessing Vendors Using the NIST Cybersecurity Framework,â presented by Randy Lindberg and Dan Banning, Director of Marketing at Quantivate.
Here are some additional resources for you to reference in the process of becoming a Vendor Assessment Jedi at your credit union:
- 1FFIEC Handbooks
- NCUA Guidance
- FDIC Guidance
- SSAE 16 Details
- National Institute of Standards and Technology (NIST) Cybersecurity Framework
- Future Considerations
- âTechnology Service Provider StrategyâThe FFIECâs members will expand their focus on technology service providersâ ability to respond to growing cyber threats and vulnerabilities.â
![]()
Quantivate is the NAFCU Services Preferred Partner for Vendor and Contract Management. Quantivate partners with Rivial Security to deliver cost-effective data security solutions that enable organizations to protect sensitive data, comply with industry standards, and gain a competitive advantage. Additional educational resources and contact information can be found at www.nafcu.org/quantivate.