Tales from the CryptoLocker: Dealing with Ransomware
Written by Andrew Morris, Regulatory Affairs Counsel
Hello and welcome to my first blog post. I'm Andrew Morris, Regulatory Affairs Counsel at NAFCU, and I help develop NAFCU's advocacy with regard to payments and cybersecurity issues. Today's blog post will focus on ransomware and address what credit unions can do to prevent, respond to and recover from these types of attacks.
As you have probably heard, a notorious variety of ransomware called "WannaCrypt" locked and disabled computer systems in at least 150 countries this past weekend. Beginning late last Friday, hospitals belonging to the U.K.'s NHS reported that their systems had been compromised, and not long after, the attack reached global proportions, with a second wave of attacks hitting countries in Asia on Monday.
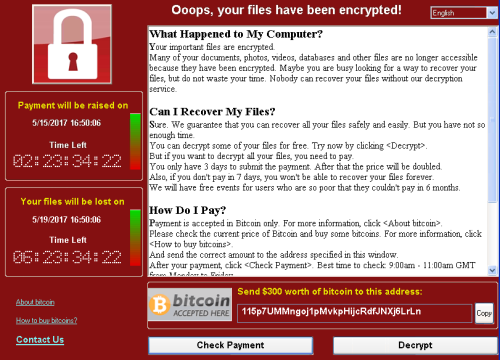
For those of you unfamiliar with the concept of ransomware, we're talking about malware that encrypts files on a computer such that a user is prevented from accessing stored data. Once the computer's files are encrypted, WannaCrypt—for example—prompts the locked-out user to pay in bitcoin to regain access. While none of this is particularly novel for ransomware, what makes WannaCrypt unique is its unusual pedigree. A growing consensus within the information security community suggests that WannaCrypt owes its shocking effectiveness to a hacking tool, or "exploit" developed by the U.S. National Security Agency (NSA).
For context, a hacking group called The Shadow Brokers previously leaked an NSA-linked exploit called "EternalBlue" to the public in April 2017, following a string of data dumps involving other NSA hacking tools. EternalBlue targets a vulnerability in Microsoft's Server Message Block (SMB) protocol which is generally used for sharing access to printers or files across a network. WannaCrypt leverages this vulnerability to infect computers connected to the same network. Fortunately, Microsoft released a security update for the SMB vulnerability back in March 2017, which has since been extended to unsupported versions of Windows, such as Windows XP. Nonetheless, Microsoft warns that the SMB attacks will likely evolve to become more resilient to detection and that customers should employ additional "defense-in-depth" strategies going forward. We won't get into a discussion of defense-in-depth, but credit unions should be aware that ransomware is constantly evolving.
Instead, we will focus on guidance NCUA has provided for credit unions dealing with extortion attacks, along with some rules that would apply to ransomware incidents. A previous compliance blog covered the basic reporting rules in Part 748 of NCUA's regulations implementing the data security provisions of the Gramm-Leach-Bliley Act of 1999. In essence, a credit union has an obligation to prevent destruction of vital records, defined in 12 CFR § 749.1, respond to incidents of unauthorized use of member information, and report "catastrophic acts" that would interrupt vital member services . See 12 CFR §§ 748.0,748.1.
Because a ransomware attack often implicates all of these obligations, credit unions must take affirmative steps to prevent ransomware attacks and have policies for notifying NCUA and affected members.
In the event that a credit union's systems are compromised with ransomware, the credit union should determine the nature of the breach and decide whether a response is warranted. If a response is necessary, the program guidelines in Appendix B to Part 748 advise credit unions to notify their NCUA Regional Director, or in the case of state-chartered credit unions, the state supervisory authority. It is also important to remember that there may be state-level notification requirements in the event of a breach.
An infected credit union may also want to contact a federal law enforcement agency. The FBI has experience dealing with ransomware attacks; however, the FBI also has a policy of not supporting decisions to pay the ransom, mainly because there is no guarantee that victims will actually regain control of their data. When seeking assistance from the FBI, victims should contact their local FBI office and/or file a complaint with the Internet Crime Complaint Center along with a description of important infection details (listed here). Credit unions are also encouraged to consult information sharing organizations and the U.S. Computer Emergency Readiness Team when dealing with cyber-attacks. FinCEN's recent Advisory on cyberevents indicates a credit union may also need to file a SAR in connection with a ransomware attack.
With respect to prevention of a ransomware attack, NCUA suggests that credit unions educate staff on how to safely interact with emails and websites. Although this may seem obvious, its importance cannot be overstated; the most common attack vector for ransomware is an email attachment coupled with some form of social engineering. Microsoft's Security Blog suggests that WannaCrypt's entry point was email, before infection spread through the SMB exploit.
NCUA also advises credit unions to maintain a robust patch-management program. In the case of WannaCrypt, Microsoft didn't push updates to customers running unsupported versions of Windows until after the attack started. Accordingly, system administrators who exercise discretion over when to apply updates should seek to patch significant vulnerabilities as soon as they are identified and exercise caution when using unsupported operating systems.
Credit unions have many resources available to help them defend against and mitigate ransomware attacks; however, the availability of leaked hacking tools means that credit unions must remain especially vigilant. NAFCU anticipated that non-disclosure of stockpiled exploits might result in significant harm, which is why NAFCU wrote a letter to the National Institute of Standards and Technology (NIST) last year warning that lack of transparency regarding discovered vulnerabilities could compromise financial sector cybersecurity. The letter urged NIST and the Presidential Cyber Commission to advocate for and adopt "more transparent procedures for determining when the government will publicly announce flaws it discovers in financial sector infrastructure," as part of the NSA's vulnerabilities equities process. You can read more about the process here.
Leaked NSA exploits may be cause for concern, but it's important to remember that most ransomware is developed "in the wild" and new varieties emerge all the time. For example, ransomware that remains dormant until it is stored on a backup drive can undermine cybersecurity resiliency efforts and potentially jeopardize business continuity planning in the event of a catastrophic attack. To improve its defense against such attacks, credit unions should engage staff to recognize the growing sophistication of social engineering strategies and the dangers of opening malicious attachments.
