Securing Your Digital Doors
By: Joshua Gideon, Manager of Audit, Risk, and Compliance | Allied Solutions
Shakespeare says to only “trust a few”. We say, never trust, only verify.
With a Zero Trust architecture (ZTA) to cybersecurity, trust is not automatically granted. Unlike trust-based networks that open the digital door for anyone who had a key at one time, a Zero Trust approach doesn’t trust login credentials alone. With alarming rises of social engineering and credential stuffing, credit unions that take a trust-based approach are more vulnerable to these types of attacks. Fraud aside, remote work and rapidly progressive technology have ramped up the critical need for this type of security structure.
Why Zero Trust?
ZTA is a strategic effort to shut and lock digital doors against bad actors’ attempts to gain access to your credit union’s data and resources. Breaches can happen off premises (and they usually do), so this strategy protects the data inside and beyond the brick and mortar perimeter.
The Core Principles of a Zero Trust Design
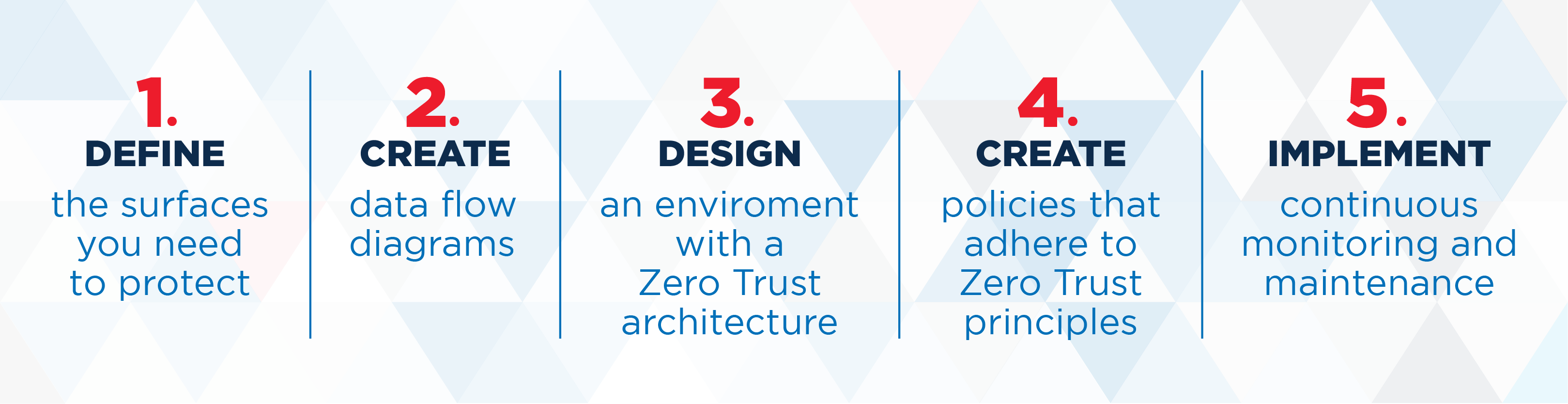
● Requires verification of every user: An inherently distrusting network relies on additional authorizations for entrance. Networks with a Zero Trust architecture have a least privileged structure, restricting sensitive data to specific areas. All credentials must be verified upon each attempted gateway entrance, regardless of privilege. No one person has access to everything. Giving access only to what someone needs to do their job will go a long way in limiting what could be stolen if someone’s credentials are compromised.
● Requires validation of every device: Similar to verification of each user attempting to gain access, Zero Trust continuously validates every device – on and off premises. Regular inspection and logging of all traffic are critical to know what is and isn’t normal on your network.
● Leverages data masking and encryption: These two functions protect at-rest and in-transit data. Data masking obscures data from unauthorized access, and encryption turns the data into unreadable characters without the correct key/code. Safeguarding data at every point is a crucial element of security that every credit union must embrace. These functions can protect data while meeting compliance standards.
Best Practices to Protect your Data from Unauthorized Access
An enterprise-wide approach to cybersecurity with a Zero Trust model will have more data security confidence and a stronger response plan in the unfortunate event of a breach. An effective Zero Trust strategy should align with your business goals and should not hinder business outcomes or efficiencies. While there are numerous tools available to secure your credit union’s digital doors, there are some best practices to keep the bigger picture in mind.
A push towards a Zero Trust architecture inside your credit union can look like:
#1: Define what needs protecting.
Use the highest revenue generating areas of your credit union as a starting point to help you identify what assets need the most protection. Build your unique Zero Trust model with these assets in mind.
#2: Automate, automate, automate.
Nearly three-quarters (75%) of data breaches are traced back to a human element - error, misuse, or abuse. The more processes that are automated through technology and artificial intelligence, the less margin for data leaks. Take inventory of what processes are being done manually across the organization. Ask your IT department to evaluate those manual processes for risk exposure and begin automating the ones that are most vulnerable.
#3: Shift the mindset.
Zero Trust is a journey, not a destination, to stronger cybersecurity– one that requires incremental changes reaching across the organization.
Cybersecurity is no longer an issue for the hallways of IT to figure out. It starts in the boardroom and requires a top-down approach. A Zero Trust architecture is an easy sell for IT. The impact on other employees is minimal, however, employees may need more communication around the increase of verification requirements that come with a ZTA.
Requiring multi-factor authentication and leveraging biometrics can serve as daily reminders for employees to be more mindful of data security.
#3: Create and review vendor contracts and policies.
Every vendor is another digital door that can be opened to gain access to your credit union’s data. The SolarWinds breach in 2020 and the recent MoveIT breach are harsh reminders that even with the tightest internal policies vendors can be a cyber vulnerability.
In addition to due diligence reviews, make sure that your executive team understands how vendors are working towards a Zero Trust architecture. Lastly, ensure that your institutional coverage also includes data breach protection in the event an attack occurs.
Final thoughts:
Today adopting a Zero Trust is a proactive, albeit optional, strategy that credit unions can implement for data security.
What if one day soon it’s a nonnegotiable?
The federal government has already mapped out how specific agencies like the CFPB, FTC, EPA, FDIC, and Department of Homeland Security must adopt a Zero Trust architecture over the next year to enhance our nation’s security. It may be that financial institutions will be required to adhere to this type of cybersecurity framework as well. And the day might be sooner than we think. Implementing a Zero Trust architecture not only secures your entire institution now, it may save your institution from financial losses down the road.
Cybersecurity deserves more than a “business as usual” approach. Learn more about Allied’s commitment to data security here: alliedsolutions.net/trust-center
[1] Verizon. 2023 Data Breach Investigation Report. https://www.verizon.com/business/resources/reports/dbir/
[2]CISA. Zero Trust Maturity Model. April 2023. https://www.cisa.gov/sites/default/files/2023-04/zero_trust_maturity_model_v2_508.pdf
