Trending Fraud Crimes and How to Combat Them
Ann Davidson, VP of Risk Consulting, Allied Solutions
Fraud exposures continue to plague our industry, many of which are tied to the expanded use of remote transaction channels. And with COVID-19, these crimes have only gotten worse.
What’s the deal with HELOC Fraud?
HELOC fraud crimes pose a potentially expensive fraud risk to credit unions, sometimes resulting in as much as six figure losses. Fraud criminals are aware of the fact that these open-ended loans can offer a lot of financial gain. They also know these loans are often not monitored as closely as an auto loan, mortgage loan, or credit card loan, and are therefore easier targets for an undiscovered attack.
HELOC attacks performed via remote channels have ramped up during COVID-19. Credit unions will want to take extra steps to review their controls surrounding HELOCs to prevent these dangerous attacks. Tune in to our podcast, How to Deter HELOC & Loan Fraud Attacks, to learn more about how these crimes take place and hear strategies for mitigating these crimes.
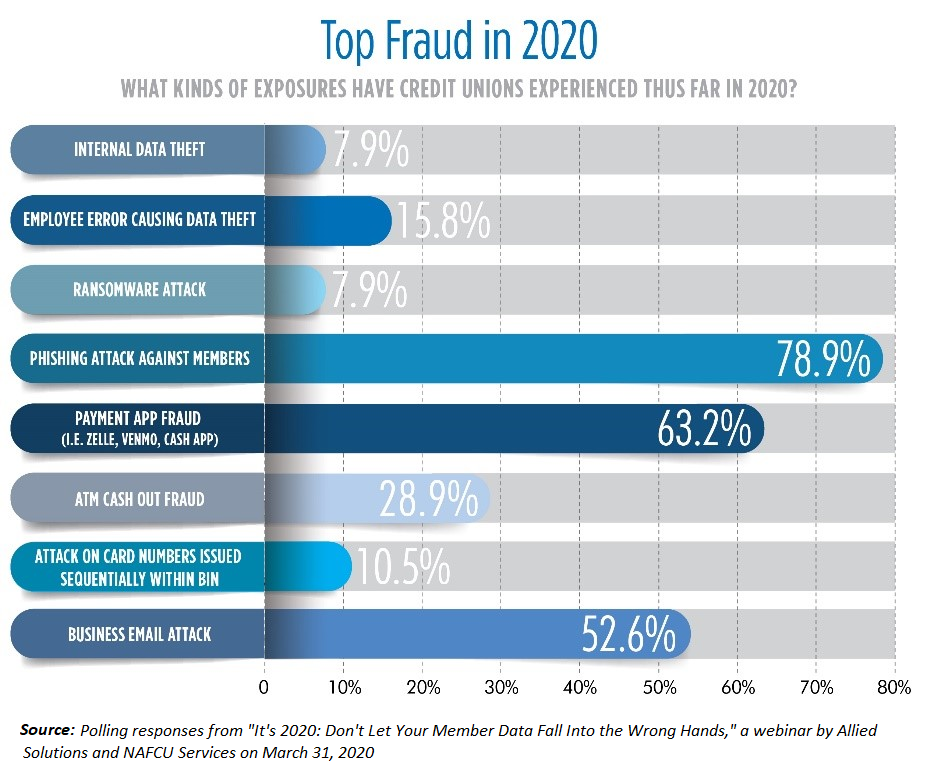
What’s going on with Online and Mobile Fraud?
Many credit unions have already experienced some kind of digital fraud attack in 2020, and the pandemic worsened these exposures as well.
While offering online and mobile solutions creates high value for credit unions and members, these channels can also open up new opportunities for fraud unless properly protected.
There are a number of digital fraud crimes impacting credit unions and members today. The most popular among these include email/phishing scams against members and businesses, remote deposit fraud, and attacks on payment app apps.
The best ways to prevent these crimes: educate members and staff, implement proactive controls, and enforce extra authentication measures. These methods can be an effective combination for preventing these fraud crimes. Listen to Tips to prevent Online & Mobile Payment Fraud to hear more about detecting and preventing attacks.
