By Brandy Bruyere, Vice President of Regulatory Compliance, NAFCU
Once again, the National Credit Union Administration (NCUA) placed cybersecurity as a focus for exams this year. In 2019, the agency will use the Automated Cybersecurity Examination Tool (ACET) for credit unions with more than $250 million in assets. The ACET largely tracks the Cybersecurity Assessment Tool (CAT) that financial regulators published a few years ago. Preparing for the cybersecurity portion of an exam can be time-consuming and challenging and often requires coordination across business units. Some credit unions choose to utilize the CAT in preparation for exams given under NCUA’s ACET, but it is not mandatory to do so.
The cybersecurity portion of an NCUA exam requires the credit union to provide the examiner with a significant amount of information. It is important to identify which staff members will be responsible for collecting all of this information. For example, the CAT measures a credit union’s inherent risk profile across five categories:
Technologies and Connection Types — includes “the number of Internet service provider (ISP) and third-party connections, whether systems are hosted internally or outsourced, the number of unsecured connections, the use of wireless access, volume of network devices, end-of-life systems, extent of cloud services, and use of personal devices.” The assessment tool lists 14 separate items in this category.
Delivery Channels — addresses “whether products and services are available through online and mobile delivery channels and the extent of [ATM] operations.”
Online/Mobile Products and Technology Services — includes “various payment services …person-to-person payments, originating automated clearing house (ACH), retail wire transfers, wholesale payments, merchant remote deposit capture [RDC] …correspondent banking and merchant acquiring activities.” There are 14 separate items in this category.
Organizational Characteristics — considers items such as “mergers and acquisitions, number of direct employees and cybersecurity contractors … the number of users with privileged access … locations of business presence,
and locations of operations and data centers.”
External Threats — considers the “volume and type of attacks,” both successful and unsuccessful, which may impact the credit union’s inherent risk, as well as the “volume and sophistication” of attacks targeting the credit union.
These general areas of operation are then used to determine the credit union’s level of risk, ranging from “least inherent” to “most inherent.” The CAT also measures a credit union’s cybersecurity maturity over five domains:
Domain 1: Cyber Risk Management — “addresses the board of directors’ oversight
and management’s development and implementation of an effective enterprisewide cybersecurity program with comprehensive policies and procedures for establishing appropriate accountability and oversight.”
Domain 2: Threat Intelligence and Collaboration — “includes processes to effectively discover, analyze and understand cyber threats, with the capability to share information internally and with appropriate third parties.”
Domain 3: Cybersecurity Controls — includes “the practices and processes used to protect assets, infrastructure and information by strengthening the institution’s defensive posture through continuous, automated protection and monitoring.”
Domain 4: External Dependency Management — “involves establishing and maintaining a comprehensive program to oversee and manage external connections and third-party relationships with access to the institution’s technology assets and information.”
Domain 5: Cyber Incident Management and Resilience — “includes establishing, identifying and analyzing cyber events; prioritizing the institution’s containment or mitigation; and escalating information to appropriate stakeholders … [and] encompasses both planning and testing to maintain and recover ongoing operations during and following a cyber incident.”
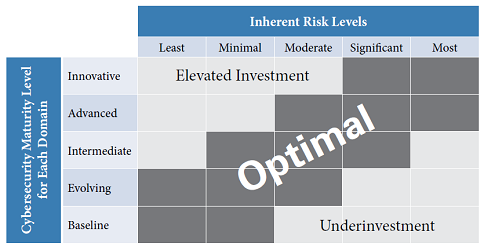 Cybersecurity maturity is measured at one of five levels for each domain. The lowest is “baseline,” which essentially represents meeting the minimum expectations set forth in regulatory guidance, followed by “evolving,” “intermediate,” “advanced” and “innovative.” The idea is for the credit union’s cybersecurity maturity to be aligned with its inherent risk. NCUA has indicated that the ACET will focus on ensuring whether credit unions meet the “baseline” across these domains. The matrix above, which was presented to the NCUA Board in 2016, indicates the agency’s expectations for a credit union’s alignment between inherent risk and cybersecurity maturity.
Cybersecurity maturity is measured at one of five levels for each domain. The lowest is “baseline,” which essentially represents meeting the minimum expectations set forth in regulatory guidance, followed by “evolving,” “intermediate,” “advanced” and “innovative.” The idea is for the credit union’s cybersecurity maturity to be aligned with its inherent risk. NCUA has indicated that the ACET will focus on ensuring whether credit unions meet the “baseline” across these domains. The matrix above, which was presented to the NCUA Board in 2016, indicates the agency’s expectations for a credit union’s alignment between inherent risk and cybersecurity maturity.
Tools such as the FFIEC IT Handbook and the FFIEC’s CAT can be useful for identifying the information a credit union needs to be prepared for cyber exams. NAFCU members may also find helpful our fillable workbook version of the CAT. Cybersecurity exam preparation can be time-consuming and technical, but NCUA has indicated that it is and will remain a priority for the agency. Collecting necessary materials, predetermining how to provide information, knowing the credit union’s weaknesses and reviewing training and education can help make these exams shorter and less disruptive for the credit union. Taking steps to get ahead of the curve can help ensure this portion of NCUA exams goes smoothly.
From the May-June 2019 edition of The NAFCU Journal magazine.
Related Content:
